I2P — one of the leading players among anonymous networks. Along with it, the projects ZeroNet, FreeNet and others flash. According to the author’s subjective assessments, I2P is the second largest project after TOR.
"The Invisible Internet Project (aka I2P) boasts complete independence of development from legal and government entities, systematic and long-term development, as well as high-quality cryptography in professional execution in production languages C++ and Java (versus student crafts in interpreted slow languages).
It is important to note that the development of two network clients (in C++ And in Java) conducted by different groups of people who are actually independent of each other. Naturally, this does not prevent them from coordinating and introducing innovations into the network protocol. Development is decentralized and discussions are transparent, which has a good effect on trust in the final product (logs IRC-chats: Team C++, java team And general chat for scheduled discussions).
If the topic of anti-censorship doesn't make you uncomfortable and you have the enthusiasm to learn something new, the spirit of I2P will appeal to you.
I2P is a peer-to-peer network that runs on top of the regular Internet as an additional encrypted transport layer (also read I2P via Yggdrasil Network). Unlike routes in a regular network, the path of traffic in I2P is unpredictable - traffic, passing from the user to the destination, overcomes an average of 6 random transit nodes, which are other I2P participants.
Unlike TOR, where the communication channel is bidirectional, I2P traffic flows through unidirectional tunnels. Thus, packets to the server go through, for example, random nodes in Russia, Kazakhstan and Europe, and the server’s response goes to the user through the USA, Canada and Japan. Every ten minutes, all encrypted communication tunnels are updated with a completely new logical pattern and cryptographic keys. At first, this is difficult to even imagine: the user does not know the physical location of the server he is accessing, and the server knows nothing about the user, thanks to transit nodes, which themselves have no way of knowing who they are serving. Read more about tunnels in a separate article. article.
The I2P transit nodes through which routes are built are not trusted servers of world organizations, institutions or anyone else, but mainly the nodes of ordinary network participants. All I2P users can be transit nodes by default. If this is news to you, don’t worry: the I2P architecture does not imply proxy output to the regular Internet, so no one will open a dubious page from your IP address in order to like it. Within the I2P network itself, the IP addresses of network participants from whom direct connections come are a priori of approximately zero significance, since such an address is just the address of a ten-minute transit link, which, even if it wants to, does not know who and what is transmitting through it.
By default, the I2P router, that is, the application for accessing this hidden network, has a very low threshold for the transit flow - only 32KB/sec (this is necessary so that users with limited traffic unknowingly do not end up with nothing after a couple of days of using I2P) . To increase the transit channel on i2pd (network client in C++), specify the value in the configuration file bandwidth = X (letter X means unlimited channel). 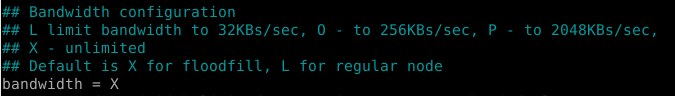
Increase transit, provide your channel for some unknown users?! Why on earth would you give up your power for the benefit of the network? This is the main question of the article, which is far from limited to altruism!
Statement of a question
We are used to launching an application only when we need its functionality. For example, open an online store page to make a purchase. It's simple.
However, when it comes to anonymity and hidden networks, the first thing that comes to mind is a timing attack. Its essence is in the synchronization of events: an observer, using special technical means, monitors the movement of traffic in a geographic region and monitors the activity of a person in a hidden network, which he wants to compare with a real person. According to some experts, calculating a specific user of the TOR network using this method requires less than five time points. This is achieved due to the fact that a limited number of people use the TOR network in a city, region or country. The main suspect is the one who is connected to the TOR network during all control measurements at the time of publication on an anonymous forum or chat. It should be especially noted that a timing attack does not imply decryption of a secure connection. The effectiveness of the method lies in the perseverance and attentiveness of the observer..
Deep traffic analysis or DPI (Deep Packet Inspection) is widely used in Internet control systems (for example, SORM in Russia). Such technologies make it possible to tell with a high probability which protocol or application the passing traffic belongs to, which, therefore, makes it possible to understand what the subscriber is doing or interested in.
Using a VPN is not very effective against a timing attack in a hidden network, since an observer can monitor the presence of traffic not only specific to the TOR network, but also make comparisons with any other anonymous information flows.
All serious projects aimed at anonymity and resistance to censorship have various tools for deceiving DPI and bypassing their protocol blocking. Without a doubt: I2P is among them. To take advantage of the full power of I2P, you do not need additional plugins, such as in TOR. Everything works by default - you just need to periodically update your I2P router (application for accessing the network) to stay on top of technology.
We will not go into complex technical details and demagoguery, since ultimately, no matter how much a user hides, if his traffic is not identical to the opening of state propaganda news portals, at the first opportunity he will become suspected of using something like that.
Why does a user need transit?
A timing attack in the general case is based on the ability of an observer to monitor the subscriber’s activity. For example, when you watch a streaming video, a large stream of data is visible to the provider. If your tariff plan includes a traffic limit, every byte you receive is charged. This clearly demonstrates the transparency of user activity for the telecom operator. Accordingly, when you sleep, the provider sees a lull.
Let's imagine that a user has placed a personal website on his computer and provided access to it from a hidden network. If someone suddenly becomes interested in who is the owner of a resource, it is unlikely that he will attempt to hack a complex transport protocol. Various techniques will be used, from social engineering to timing attacks..
Simply put, a timing attack can be carried out like this: thousands of requests will be sent to a hidden site at the same time and they will observe where the burst of activity appeared on the regular Internet, that is, where all these requests arrived. The task is large-scale, but the elusive Joe is elusive only as long as no one needs him.
Let’s imagine that no one visits the site and the activity of the server’s Internet channel is practically zero. Suddenly, the observer simultaneously sends a large number of requests to the server from different devices (performs a primitive DDoS attack). Passing through the intricate tunnels of the hidden network, all requests reach the server and its real network channel experiences an obvious increase in load.
If the server you are looking for is physically located in a controlled segment of the Internet, for example, on the territory of the country whose intelligence services are conducting the operation, several matches at different times of the day will be enough to say with confidence where the hidden site is actually hosted.
The timing attack is applied in approximately the same way to ordinary users: virtual activity is compared with real bursts of subscriber activity. In practice, everything is somewhat more complicated, but these are nuances that do not interest us in this article..
Now let’s imagine that the activity of the Internet channel of a server or user device does not depend in any way on its useful activity (that is, real actions). This is possible if the network channel is always under load. In this case, observations from the outside are useless, since real activity is nothing more than an error in the turbulent and constantly jumping flow of transit traffic. This phenomenon can be compared to noise: if music is playing loudly at home, you can scream until you are hoarse, and when you meet your neighbors they will only say that you are listening to Baskov too loudly.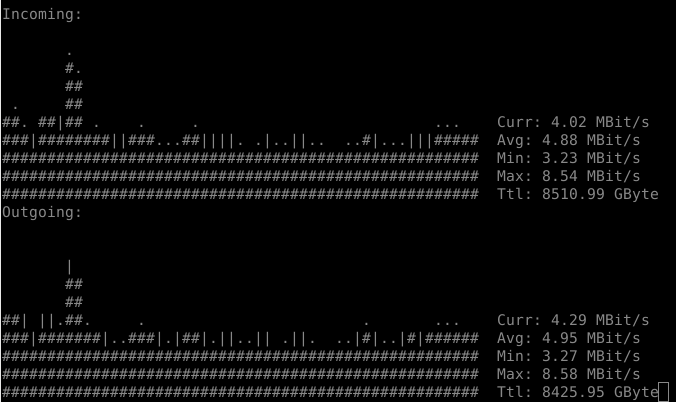
The screenshot below shows the difference between Sent And Transit in the i2pd web console, from which it is clear that out of 9TiB of outgoing packets, the server gave only about 6GiB of its real information to users who contacted it.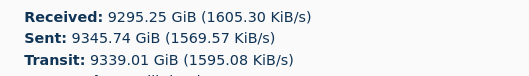
The fact that these 6 gibibyte it is impossible to isolate from the entire encrypted stream when observed from the outside, and there is a clear illustration of the benefit of a large transit as a guarantor against possible timing attacks.
With a large number of transit tunnels, an I2P router builds its own tunnels using routers, together with which it makes other people’s transit tunnels. Overlaying your information on the tunnels of other participants turns I2P router connections into an insoluble tangle of encrypted labyrinths that cannot be analyzed by anyone..
How to get a lot of transit
First, pay attention to the I2P router settings that we talked about at the beginning of the article.
I2P routers communicate directly with each other. Therefore, for your node to receive a lot of transit, it must be easily accessible. In other words, you must have a dedicated IP address to receive calls from outside, but for a home PC or smartphone with a “gray” IP address, the small transit that will still happen is a good help for the error in observations from the outside. Despite the lack of a dedicated IP address, I2P routers are still able to establish direct contact (you can read about this here).
Each I2P router has a profiling function that helps select reliable nodes as transit nodes - the more stable the online of your node, the more preferable it is for other participants to build tunnels.
If for some reason you have to turn off your “boosted” server or PC for a long time, you will provoke many unsuccessful connection attempts from other network participants, which is why your status as a reliable node will gradually change to unreliable. As a result, when you start up again, transit traffic will drop significantly. In i2pd, the profiled information is considered relevant for three days (about the same in the Java version), after which the I2P router is again ready to check the quality of the previously unreliable router and, if it has improved, mark it with a quality mark. As an alternative, you can quickly start from scratch by deleting the router identifier (file router.info) and restarting the I2P router. In Debian, this file is located by default in the folder /var/lib/i2pd/.
Open Kingstons
The more nodes there are in I2P, the more distributed and stable the network is before analysis. The more traffic on each node, the more anonymous the entire network. By including transit for your purposes, you help everyone. By helping everyone, you ensure your anonymity.
If you have not only unlimited Internet, but also disk space, you can make some noise with double benefit: read the article about torrents in I2P.